
This page was already viewed 5895times
Free linux iptables firewall online generator

Summary
[I] General presentation
*What is iptables?Iptables is a well-known and widely used free software that provides a command-line interface to configure the Linux (debian/ubuntu flavor) embedded firewall kernel module a.k.a Netfilter. Having a network filtering policy is maybe THE most important step to protect a system from cybersecurity threats. Some concurent/equivalent software, like UFW appearing in these recent years, claims to facilitate "admin'sys" jobs with easier requests, however this doing at a price of a very BIG reduction of the firewall confs' capabilities. This is clearly not wishable when needing a very strong security policy.
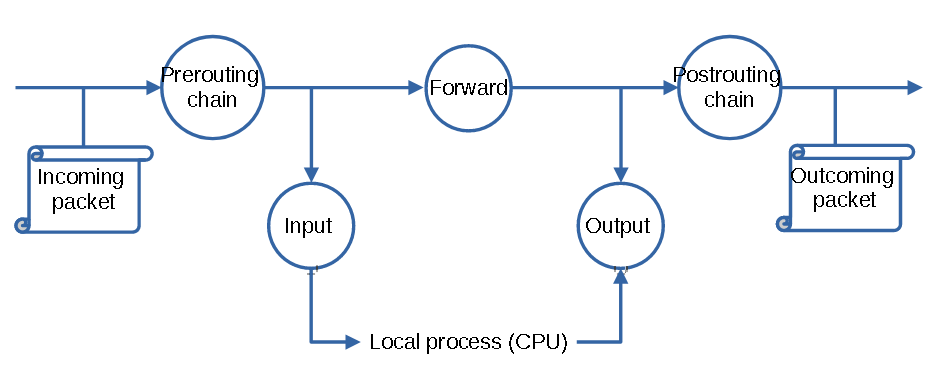
*How does it work?Thanks to this software, system administrators are able to deeply configure their network policy via a ruling system applied to specific "chains". By default, the netfilter firewall defines 5 distincts chains (PREROUTING, INPUT, FORWARD, OUTPUT, POSTROUTING) targeting the standard communication states and covering the most part of the needs. Users are totally able to produce and make use of custom other chains for various other needs (I.e: NAT chain). The term 'filter' is usually identified for the chain. The following picture is a simpified picturization of the linux firewall network packet flow and the chain principle.
 *Conclusion
*Conclusion
Iptables is a very powerfull tool to configure the netfilter firewall, however, it is very time consuming to set-up a strong policy. Finseckto offers you a very easy and powerfull API to help configuring the netfilter firewall by automatically generating a proper and precise iptables based script depending on your needs.The following sections will guide you through the Finseckto online iptables API.
Also, visit the Firewall BAR, Our beautiful free online Linux iptables script generator.
[II] Iptables firewall API
*API presentationThe following paragraph explains the usage of the finseckto iptables online API. This API allows to produce a working linux bash script making use of the iptables command-line to produce the requested firewall policy. The usage of this API is optimized for commandline download tools such as WGET or CURL (Linux)
Adding the 'api' tag in the URL request is the API start point (finseckto.com/firewall?api). Using api=X will get the various API help pages when replacing X by one of the allowed values: help, protolist and tasklist (note that h, p & t are also working).
Lets start by requesting the API main HELP page. Open a terminal and prompt the following:
client@linux:#wget -q 'https://finseckto.com/firewall?api=help' -O - |cat Copyright © 2021 Finseckto (stack2me, talk2me, tuto2me) [+]Iptables online generator API. [+]help available at: wget -q 'https://finseckto.com/firewall?api=help' -O - |cat [+]This page will guide you through the API usage [+]The usage of this API is optimized for commandline download tools such as WGET or CURL (Linux) [+]USAGE wget -q 'https://finseckto.com/firewall?api&PROTOCOL=TYPE[&PROTOCOL=TYPE]' -O script-iptables.sh [-]PROTOCOL: a supported IP protocol: FTP, SSH, HTTPS, etc... [-] complete list at: ?api=protolist [-]TYPE: an host type: client or server [-] Allowed values: c, cli, client, s, serv, server [+]EXTRA TASKS wget 'https://finseckto.com/firewall?api&tasks=TASK' -O script-iptables.sh [-]TASK: a supported extra task: d, p, l, s [-] d: drop all trafic by default [-] p: preserve already established trafic [-] l: whitelist localhost trafic [-] s: save configuration at startup [-] complete detailed list at: ?api=tasklist
The API global logic is presented as the string: ?api[&tasks=TASK]&PROTOCOL=TYPE[&PROTOCOL=TYPE]'. The request shall always start with the '?api' tag. Each requested protocol shall be sperated by a '&' character. The presence of brackets ('[]') refers to an optional sequence.
When requesting a protocol, a communication type shall also be given. A type consists in the 2 options: 'client' or 'server' (formerly c or s) where 'server' is the default logic if nothing is expressed. A good iptables policy will adapt its behaviour depending of the packet state sequence regarding its client or server status.
As an exemple, https=s will produce an iptable script allowing https adapted for the server side. In the same logic, telnet=c,dns=c, syslog=c, vnc=c or whatever=c would produce an adapted iptable script allowing network flows for the defined protocol in the client behaviour.
The complete protocols list supported by the API is listed in the ?api=p section. Prompt the following:
client@linux:#wget -q 'https://finseckto.com/firewall?api=p' -O - |cat [+]SUPPORTED PROTOCOLS LIST FTP [21] SSH [22] TELNET [23] DNS [53] DHCP/BOOTP [67] TFTP [69] HTTP [80] POP [109] IMAP [143] SNMP [161] LDAP [389] HTTPS [443] SYSLOG [514] LDAPS [686] VNC [5800]
Moreover, some particular special functions are implemented by the API and produces scripts for dedicated tasks. The 'tasks' parameter allows to enable various provided tasks, under the form of tasks=TASKLIST. Where TASKLIST is a list of single characters corresponding to the tasks we want to activate.
- Drop all trafic by default: This feature configures the default policy to DROP all IP packets and is applied to the INPUT, OUTPUT and FORWARD chains. This feature is very important as it guaranty the white-listing enabled policy. It is enabled by passing the 'd' option to the tasks parameter.
- Preserve already established connections: This feature prevent the current established connections from being dropped and so may prevent from being remotely 'banned' by iptables misconfigurations. This configuration is useful as a safety measure. It is enabled by passing the 'p' option to the tasks parameter.
- Whitelist localhost: This feature allows all local trafic (lo interface) on your system. Many system services communicates through the local interface and blocking localhost trafic could cause huge instability. Indeed, preserving the system from blocking localhost trafic will mostly prevent bad behaviours.It is enabled by passing the 'l' option to the tasks parameter.
- Save the current iptables configuration and set at startup (/!\package iptables-persistent required/!\). This feature requires the enabling and usage of /etc/rc.local startup script. It requires the presence of iptables-save commandline (package: iptables-persistent). It requires the presence of iptables-restore commandline (package: iptables-persistent). This feature is enabled by passing the 's' option to the tasks parameter.
The detailed tasks special arguments are listed in ?api=t. Prompt below:
client@linux:#wget -q 'https://finseckto.com/firewall?api=t' -O - |cat [+]EXTRA TASKS LIST [-]Request an extra feature using the ?tasks=TASK [-] d: drop all trafic by default [i] This feature configures the default policy to DROP all IP packets [i] Applied to the INPUT, OUTPUT and FORWARD chains [-] p: preserve already established connections [i] This feature prevent the current established connections from being dropped [i] May prevent from being remotely 'banned' by iptables misconfigurations. [-] l: whitelist localhost [i] This feature allows all local trafic (lo interface) on your system. [i] Many system services communicates through the local interface and blocking localhost trafic could cause huge instability. [i] Indeed, preserving the system from blocking localhost trafic will mostly prevent bad behaviours. [-] s: save the current iptables configuration and set at startup [i] This feature requires the enabling of /etc/rc.local startup script [i] It requires the presence of iptables-save commandline (package: iptables-persistent [i] It requires the presence of iptables-restore commandline (package: iptables-persistent [i] install iptables-persistent
To facilitate the usage of the API, the section below presents some simple examples.
[III] Examples
*Usecase N°1Generate and apply an iptables policy wich block all trafic by default, allow localhost, preserve established connections, save and set at startup, Allows ssh,ftp,http,https as clients requests.
*Usecase N°2client@linux:#wget -q 'https://finseckto.com/firewall?api&tasks=dlps&ssh=c&ftp=c&http=c&https=c' -O script.shclient@linux:#bash script.sh
Generate and apply an iptables policy wich block all trafic by default, allow localhost, save and set at startup, allows ssh,ldap,ldaps as server and vnc as client requests
*Usecase N°3client@linux:#wget -q 'https://finseckto.com/firewall?api&tasks=dls&ssh&ldap=s&ldaps&vnc=c' -O script.shclient@linux:#bash script.sh
Generate and apply an iptables policy wich block all trafic by default, allows ssh,ftp,http and https as server requests
*Usecase N°4client@linux:#wget -q 'https://finseckto.com/firewall?api&tasks=d&ssh&ftp&http&https' -O script.shclient@linux:#bash script.sh
Generate and apply an iptables policy wich block all trafic by default, allows ssh,ftp,http,https,ldaps as clients requests
*Usecase N°5client@linux:#wget -q 'https://finseckto.com/firewall?api&tasks=d&ssh=c&ftp=c&http=c&https=c&ldaps=c' -O script.shclient@linux:#bash script.sh
Generate and apply an iptables policy wich block all trafic by default, allows ssh,ldap,ldaps,snmp and syslog as server requests
*Usecase N°6client@linux:#wget -q 'https://finseckto.com/firewall?api&tasks=d&ssh&ldap&ldaps&snmp&syslog' -O script.shclient@linux:#bash script.sh
Generate and apply an iptables policy wich drop all trafic by default
*Usecase N°7client@linux:#wget -q 'https://finseckto.com/firewall?api&tasks=d' -O script.shclient@linux:#bash script.sh
Generate and apply an iptables policy wich allow localhost trafic
*Usecase N°8client@linux:#wget -q 'https://finseckto.com/firewall?api&tasks=l' -O script.shclient@linux:#bash script.sh
Generate and apply an iptables policy wich allows localhost trafic and preserve already established connections
*Usecase N°9client@linux:#wget -q 'https://finseckto.com/firewall?api&tasks=lp' -O script.shclient@linux:#bash script.sh
Generate and apply an iptables policy wich blocks all trafic by default, allow localhost, preserve already established connections and save configuration to load at startup.
client@linux:#wget -q 'https://finseckto.com/firewall?api&tasks=dlps' -O script.shclient@linux:#bash script.sh